Enable SSL VPN using only certificates for authentication.
REQUIRED CERTIFICATES:
The CA Cert needs to be installed on the Fortigate into the Remote CA Certificates section.
The corresponding client pfx certificate needs to be installed into the local computer certificate store for each VPN client device.
The following link is useful if you want to generate certificates for testing: https://securitynetworkinglinux.wordpress.com/2021/01/25/how-to-configure-a-ssl-vpn-with-certificate-authentication-on-a-fortigate/
ON THE FORTIGATE:
Create a peer user which references the CA Certificate. It should also reference the subject field from the Certificate
config user peer
edit "pki0"
set ca "CA_Cert_3"
set subject "CN =.moorfields.nhs.uk"
next
end
Create a user group and add the peer user account.
config user group
edit "CERT-AUTH"
set member "pki0"
next
end
Configure the SSL VPN with the following settings.
config vpn ssl settings
set reqclientcert enable
set servercert "Fortinet_Factory"
set tunnel-ip-pools "SSLVPN_TUNNEL_ADDR1
set source-interface "wan1"
set source-address "all"
set source-address6 "all"
set default-portal "no-access"
config authentication-rule
edit 1
set groups "CERT-AUTH"
set portal "tunnel-access"
next
end
end
Configure relevant SSL policy rules specifying the CERT-AUTH group as the user.
ON FORTICLIENT OR EMS SERVER.
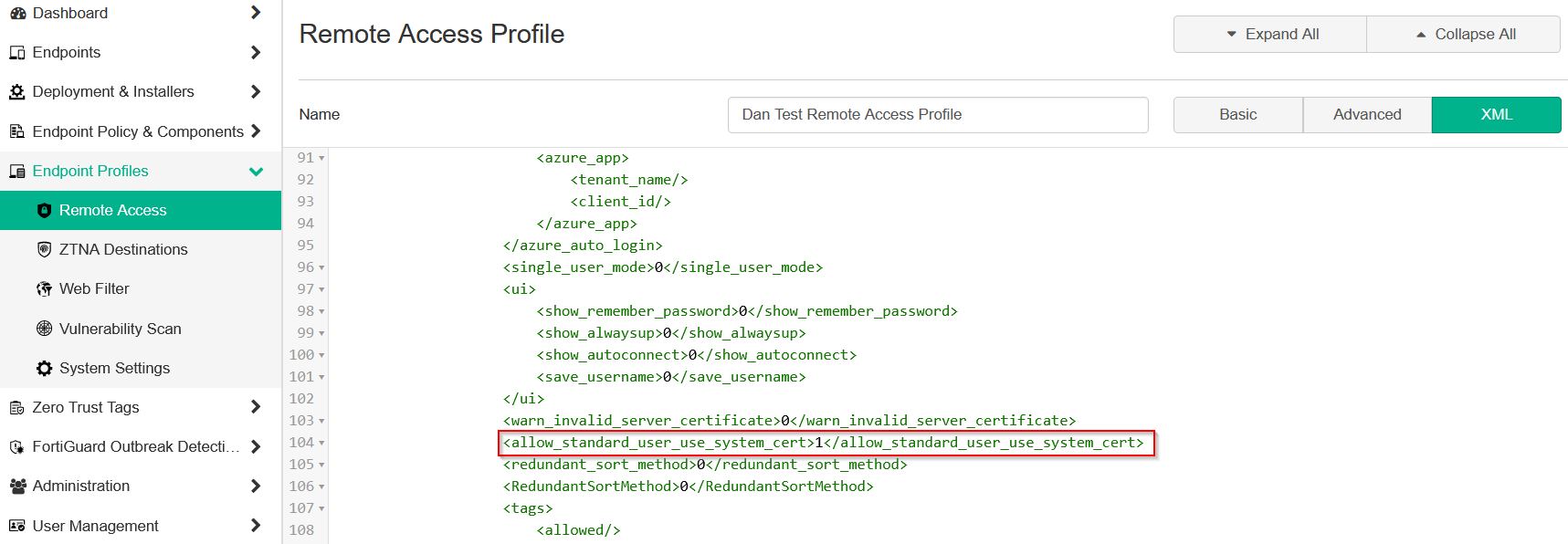
Configure the Forticlient remote access profile with relevant settings. Then edit the XML config backup file. Add the following line to allow local access to the PC certificate store.
<use_win_local_computer_cert>1</use_win_local_computer_cert>
Or edit the Remote Access profile on EMS setting it from 0 to 1.
.png?height=120&name=advatek_final-updated-blk-1%20(1).png)